Aviation Security Identification Cards (AU)
Saturday, Oct 5, 2024 | 9 minute read | Updated at Saturday, Oct 5, 2024
Australian Aviation Security Identification Cards (ASICs) are a vital part of the nation’s airport security infrastructure. They are primarily used to ensure that individuals with access to restricted areas of Australian airports have been properly vetted. ASICs were introduced to provide an additional layer of security following international recommendations, ensuring that those with access to secure aviation environments do not pose security risks.
The Aviation Security Identification Card (ASIC) is an identification card issued to individuals who require access to secure areas of Australian airports. Introduced in 2005, the ASIC system is designed to meet international aviation security standards, aligning with International Civil Aviation Organization (ICAO) recommendations. The main purpose of ASICs is to restrict access to areas such as tarmacs, baggage handling zones, and secure terminals to authorized personnel only.
Purpose
- Access Control - ASICs ensure that only authorised individuals are granted access to secure areas of Australian airports
- Background Verification - ASICS require a background check from AusCheck to be conducted, ensuring that individuals in secure areas are not a significant threat to aviation security
- Regulatory Compliance - ASICs fulfil the Australian Government’s compliance requirement with Annex 17 of the Convention on International Civil Aviation.
Types
There are 3 types of ASIC cards
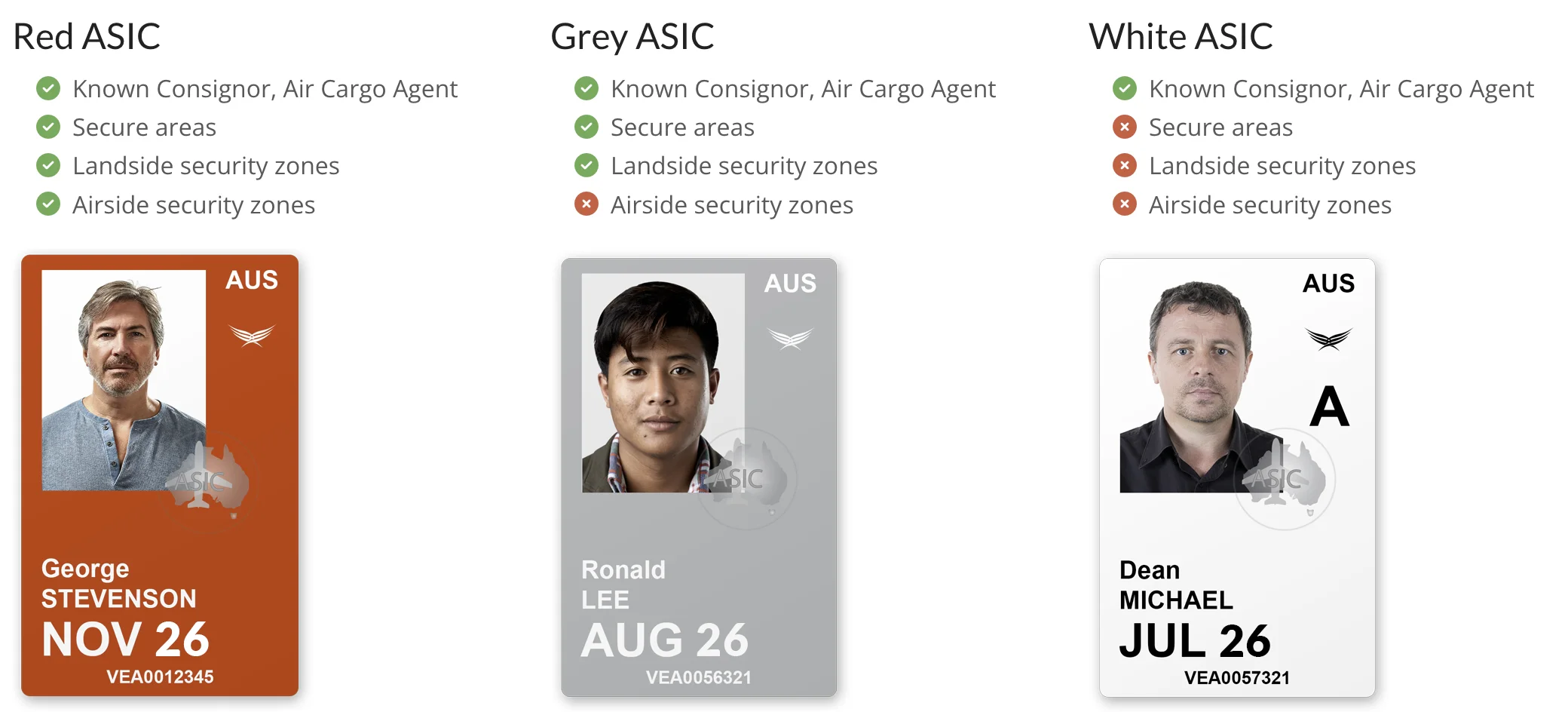
Red
To obtain a Red ASIC, applicants must pass a rigorous background check, which includes a National Police Check and an assessment of any potential security risks by the Australian Government. Applicants also need to prove their operational need for access to secure areas of the airport.
The Red ASIC is intended for individuals who need regular and unrestricted access to secure zones of security-controlled airports, such as airside areas, which include runways, taxiways, and baggage handling areas. It provides unescorted access to secure areas, allowing holders to freely move within these high-security zones without the need for an escort.
Red ASIC holders must always wear their card visibly while in restricted areas and adhere to all security protocols, including complying with airport security staff. They are also required to report lost or stolen cards immediately, and must undergo renewal processes every two years, including background rechecks.
White
To qualify for a White ASIC, individuals need to undergo a background check similar to that of a Red ASIC, though it is less stringent regarding airside access. Proof of employment or a legitimate operational need is required, but access is limited to non-airside areas.
The White ASIC is designed for individuals who require unescorted access to landside areas of the airport, which are not as security-sensitive as airside areas. This includes areas such as public terminals where passengers are processed. Holders of a White ASIC can move freely in non-secure areas of the airport but cannot access airside areas unless accompanied by an individual with the appropriate access rights.
Like with Red ASICs, white ASIC holders must keep the card visible at all times when on duty, comply with airport security regulations, and report any loss or theft of their card. The card must be renewed every two years, with a new background check conducted at each renewal.
Grey (Visitor Identification Card)
Individuals requiring a Grey ASIC must undergo a basic identity verification and need to demonstrate the purpose of their temporary visit to secure areas of an airport. They do not need to pass the same level of background checking as Red or White ASIC holders since they are always escorted.
The Grey ASIC is meant for temporary visitors or workers who need limited access to secure airport areas. It is commonly issued to subcontractors, suppliers, or temporary staff for short-term projects or official visits. A Grey ASIC permits escorted access only to secure areas, meaning the holder must be accompanied at all times by an authorized Red ASIC holder while inside restricted zones.
Grey ASIC holders must comply with security protocols, wear the card visibly at all times, and ensure they are accompanied by an authorized escort whenever they are within secure areas. Grey ASIC cards are generally issued for a short period, and holders must return the card once their visit or work is complete.
Issuance
ASICs can be issued by any of 16 different organisations:
| Organisation | ASIC Types | Limitations |
|---|---|---|
| AMS Australia | Red, Grey, White | |
| Airport Security/Aviation Security ID | Red, Grey, White | |
| Air Services Australia | Red, Grey, White | Only for employees and contractors |
| Aviation ID Australia | Red, Grey, White | |
| Cairns Airport | Red, Grey | Must also prove “genuine operational need to be on Cairns Airport” |
| Leidos Airborne Solutions | Red, Grey, White | |
| Gold Coast Airport | Red, Grey, White | Only valid for local area and “other established airports” |
| Hobart International Airport | Red, Grey, White | Employees, stakeholders, & tenants only |
| IPEC (Team Global Express, formerly TOLL) | Red, Grey, White | Only for employees and contractors |
| Mackay Airport | Red, Grey | Only valid for local area |
| Melbourne Airport | Red, Grey | |
| Perth Airport | Red, Grey, White | Only valid for local area |
| QANTAS | Red, Grey | Only for employees and contractors |
| Sydney Airport | Red, Grey | Must also prove “genuine operational need to be on Sydney Airport” |
| Virgin Australia Airlines | Red, Grey | Only for employees and contractors |
| Veritas (VEA) | Red, Grey, White |
Since 2023, AusCheck has been attempting to move away from these providers and centrally manage all ASICs through the “AusCheck Issuing Body”. As of March 2024, only Adelaide Airport has moved to this system.
Security Features
Photographic ID
The most prominent component of the ASIC is a photograph of the cardholder, serving as an essential security feature for visual verification. The inclusion of a high-quality image allows security personnel to quickly identify individuals and confirm that they match the person authorized to hold the card. This feature helps prevent the unauthorized use of a card, as it is immediately evident if the photograph does not match the person presenting it. This visual verification process is crucial in ensuring that only authorized individuals gain access to secure areas, providing a fundamental layer of identification security.
Holograms and Microtext
ASIC cards are embedded with holograms and microtext, which serve as anti-counterfeiting measures. Holograms are optical security features that are difficult to replicate without specialized equipment, making it challenging for counterfeiters to produce fake cards. Additionally, microtext, which consists of very small printed text, is not easily visible to the naked eye but can be examined for authenticity. These features are designed to be complex enough to resist duplication, ensuring that any attempts to forge an ASIC card would require considerable resources and expertise, thereby deterring unauthorized duplication and enhancing the card’s credibility.
Unique Card Numbers
Each ASIC card has a unique identification number that helps verify its authenticity. The unique card number is linked to the cardholder’s personal details in the issuing body’s security database, allowing authorities to cross-reference the card’s details with its legitimate holder. This system ensures that lost or stolen cards can be flagged, and access can be immediately revoked. The unique number also aids in tracking the issuance and expiry of cards, providing a robust method for managing the lifecycle of each card while preventing the duplication of card data for fraudulent purposes.
Tamper-Evident Design
ASIC cards are created with tamper-evident materials, meaning that any attempt to alter the card will leave visible signs of tampering. This feature includes elements like specialized lamination or a fragile construction that breaks apart if the card is tampered with. This helps ensure the integrity of the cardholder’s details—if any unauthorized modification is attempted, it will be clearly apparent, making it difficult for individuals to alter or forge card information. This tamper-evident design is crucial for maintaining the authenticity of the card and protecting against any alterations that could compromise airport security.
Key Weaknesses
Fraudulent Use and Counterfeiting
One of the major weaknesses of the ASIC system is its vulnerability to fraudulent use and counterfeiting. Despite the security features like holograms and microtext, there have been instances of sophisticated counterfeiters managing to create convincing fake ASIC cards. This can be attributed to the advancement in technology that makes it easier to replicate holographic images and print fine details. Fraudulent ASIC cards in circulation pose a significant risk to aviation security, as unauthorized individuals could potentially gain access to restricted areas, bypassing security protocols. The challenge of effectively identifying counterfeit cards makes the ASIC system susceptible to breaches, particularly in cases where visual checks are insufficient or poorly conducted.
There have been some documented cases of vulnerabilities and exploitation regarding Australian ASIC cards. One notable incident involved a data breach at Aviation ID Australia, a company responsible for issuing ASICs. The breach exposed sensitive personal information, including names, addresses, and identification numbers. The breach happened due to unauthorized access to the company’s website, which exposed applicant data through weak security measures such as an unsecured login page. This incident has highlighted the importance of improved cybersecurity measures for companies handling such sensitive data to ensure the integrity of airport security systems.
Another weakness in the ASIC system is its inability to effectively mitigate insider threats or promptly revoke access following changes in employment status. Since the ASIC card is issued for a two-year period, background checks are not conducted continuously. This means that individuals whose personal circumstances have changed, possibly increasing their risk profile, may still retain their access rights. Additionally, delays in revoking access create a significant security risk, as unauthorized individuals can exploit their prior access to secure zones, thereby compromising airport security.
Lack of Digital Authentication
ASIC cards are primarily verified through visual checks by security personnel, which introduces a risk of human error. Security guards must verify that the photograph and information on the card match the individual presenting it. However, this process can be inconsistent and prone to mistakes, particularly during busy periods when airport staff may be overwhelmed. Additionally, poorly trained personnel may not conduct these checks diligently, allowing unauthorized individuals to pass through with fraudulent or borrowed cards. The reliance on visual checks without sufficient technological support creates a significant vulnerability, as human oversight or negligence can compromise the effectiveness of the ASIC system.
While some ASIC cards have barcodes or QR codes, they lack comprehensive digital integration such as biometric data or smart card technology that could provide enhanced security. Advanced systems could cross-check the cardholder’s identity with facial recognition or fingerprint verification, adding an extra layer of assurance. The current reliance on physical cards limits the ability to use automated systems that could better detect fraudulent activity or expired cards, making the system less effective compared to more technologically advanced access control methods.
STAR Rating
- Security: ASICs are not secure. In the SecEDU conference, it was demonstrated that a laminated printout of an image of an ASIC was able to get through most screenings, and there is no onboard authentication (such as a microchip). 1/5
- Throughput: ASICs make up for their security in throughput. The regulations around wearing them above waist height, and the prominent date of expiry, mean that they can receive a baseline check at a glance simply by knowing what month and year it is. 5/5
- Accuracy: ASICs are still vulnerable to type 1 errors, where a fraudulent card could be used to get through a security checkpoint. However, type 2 errors are next to impossible (short of forgetting the card itself at home). 2/5
- Readiness: Australian Border Force, the ATSB, and airport security all work in conjunction to ensure that the majority of terrorism and bioterrorism threats are mitigated in Australia. 4/5
